 It is the perfect time to follow some security tips for both your home and work. RISC Management and Consulting put together some publicly available tips and tools. Our goal is to bring awareness and assist in building a Culture of Cybersecurity through training and providing resources. To view our solutions from vulnerability assessments to workforce training visit our site.
It is the perfect time to follow some security tips for both your home and work. RISC Management and Consulting put together some publicly available tips and tools. Our goal is to bring awareness and assist in building a Culture of Cybersecurity through training and providing resources. To view our solutions from vulnerability assessments to workforce training visit our site.

-
Lee Kim had an inspiring talk on “Sharing with Care: The Key to Healthcare Cybersecurity is You” at the ISC2 Security Congress 2018.
-
75.7% said they had a recent security incident based on the 2018 HIMSS Cybersecurity Survey.
The Importance of Technology Research and Findings
The Department of Homeland Security’s (DHS) Enhanced Cybersecurity Services (ECS) program is an intrusion prevention capability that is available to U.S.-based entities and State, Local, Tribal, and Territorial (SLTT) organizations. DHS partners with service providers that build and maintain classified systems capable of protecting ECS customer networks against unauthorized access, exploitation, and data exfiltration.
The two statistical findings below came from two national studies – a national survey on online behaviors and attitudes for the National Cyber Security Alliance (NCSA) and the Anti-Phishing Working Group (APWG) and a two-phase national survey on messaging surrounding online privacy for NCSA.
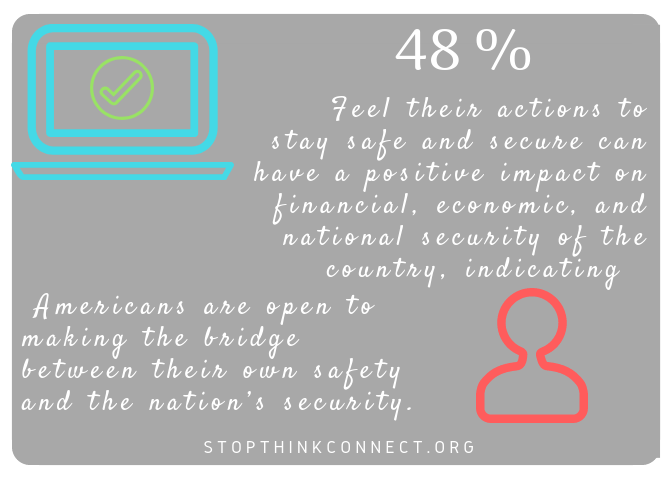
In addition, Keri Pearlson, MS, DBA – MIT Sloan School of Management and her team shared research from MIT’s Sloan School on components necessary to build a culture of cybersecurity and provide managerial mechanisms to enable every employee’s ability to increase cybersecurity. 
Techniques used by smart phone ransomware based on data analysis from Nokia’s Threat Intelligence Center. The Nokia Threat Intelligence Lab focuses on the behavior of malware network communications to develop detection rules that identify malware infections based on command-and-control communication and other network behavior.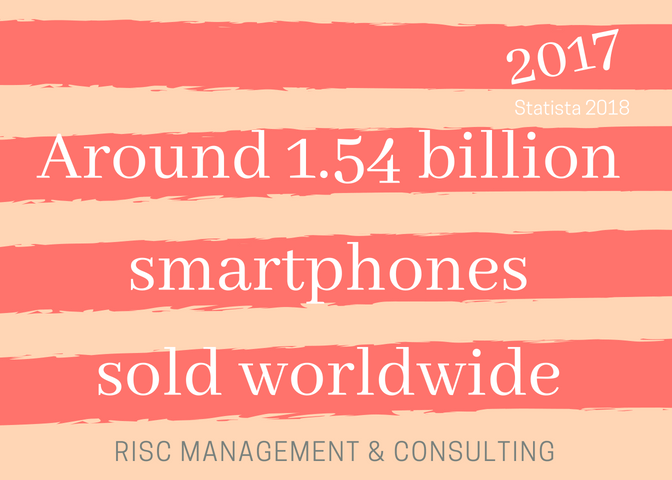
Don’t be part of the growing cyber incidents, BE INFORMED!
Read on, View the Good, the Bad, and the Worse!
2018 Data Breach Investigations Report states that 92 percent of malware is still delivered by email.
Facebook says millions of users who thought they were sharing privately with their friends may have shared with everyone because of a software bug.
Hands off my data! 15 default privacy settings you should change right now.
Are you creeping on my DNA? When it comes to privacy, stakes are high for the relatively new field of consumer genomics.
“They frequently go through online platforms like Google and blogs, to hide themselves and give investigators the impression it is a normal platform or tool, and thus to ignore its background actions,”.
Avoiding Social Engineering and Phishing Attacks. In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems. An attacker may seem unassuming and respectable, possibly claiming to be a new employee, repair person, or researcher and even offering credentials to support that identity. However, by asking questions, he or she may be able to piece together enough information to infiltrate an organization’s network.
Report Incidents, Phishing, Malware, or Vulnerabilities.
Chinese Intelligence Officers and their recruited hackers and insiders conspired to steal sensitive commercial aviation and technological data for years.
June 2018 OCR Cybersecurity Newsletter – Guidance on Software Vulnerabilities and Patching.
Georgia man has been arrested on federal charges he carried out an e-mail spoofing scheme that cost Sedgwick County $566,000, U.S. Attorney Tom Beall said.
Want more online privacy? Brave, the ad-blocking browser, has a new way to get it on the web.
Anthem Pays OCR $16 Million in Record HIPAA Settlement Following Largest U.S. Health Data Breach in History, Anthem, Inc. has agreed to pay $16 million to the U.S. Department of Health and Human Services, Office for Civil Rights (OCR) and take substantial corrective action to settle potential violations of the Health Insurance Portability and Accountability Act (HIPAA) Privacy and Security Rules after a series of cyberattacks led to the largest U.S. health data breach in history and exposed the electronic protected health information of almost 79 million people. The $16 million settlement eclipses the previous high of $5.55 million paid to OCR in 2016.
Several security research teams recently announced a vulnerability in most computer processor chips sold for at least the previous 10 years.
Department of Homeland Security (DHS) providing how to socialize online, protect your own computer at home including your children’s privacy while online, advice for parents for different ages, under their STOP.THINK.CONNECT.TM Chatting with Kids About Being Online.
How To Survive A Ransomware Attack — And Not Get Hit Again
Email is still the problem. Are you tired of sending out nagging notes to company staffers insisting that they not just click on any old email attachments? Well, we’re afraid you’re going to have to keep at it, because according to Verizon’s 2018 Breach Investigations report, 92 percent of malware is still delivered by email.
Publicly Available Tools Seen in Cyber Incidents Worldwide
This report is a collaborative research effort by the cyber security authorities of five nations: Australia, Canada, New Zealand, the United Kingdom, and the United States. See highlight from the five publicly available tools, which have been used for malicious purposes in recent cyber incidents around the world. The five tools are:
- Remote Access Trojan: JBiFrost
- Webshell: China Chopper
- Credential Stealer: Mimikatz
- Lateral Movement Framework: PowerShell Empire
- C2 Obfuscation and Exfiltration: HUC Packet Transmitter
SIMPLE TIPS from the Department of Homeland Security
Cybersecurity is present in every aspect of our lives, whether it be at home, work, school, or on the go. Regardless of one’s technical ability or background, there are simple steps everyone can take to stay safe online.
Protect yourself online and help to make the Internet safer and more secure by following these simple tips from the Stop.Think.Connect.™ Campaign:
- Enable stronger authentication. Always enable stronger authentication for an extra layer of security beyond the password that is available on most major email, social media and financial accounts. Stronger authentication (e.g., multi-factor authentication that can use a one-time code texted to a mobile device) helps verify that a user has authorized access to an online account. For more information about authentication, visit the new Lock Down Your Login Campaign.
- Make your passwords long & strong. Use complex passwords with a combination of numbers, symbols, and letters. Use unique passwords for different accounts. Change your passwords regularly, especially if you believe they have been compromised.
- Keep a clean machine. Update the security software, operating system, and web browser on all of your Internet-connected devices. Keeping your security software up to date will prevent attackers from taking advantage of known vulnerabilities.
- When in doubt, throw it out. Links in email and online posts are often the way cyber criminals compromise your computer. If it looks suspicious (even if you know the source), delete it.
- Share with care. Limit the amount of personal information you share online and use privacy settings to avoid sharing information widely.
Excerpts from the Stay Safe Online by the National Cyber Security Alliance
“When dealing with cybercrime, an ounce of prevention is truly worth a pound of cure. Cybercrime in its many forms (e.g., online identity theft, financial fraud, stalking, bullying, hacking, email spoofing, information piracy and forgery and intellectual property crime) can, at best, wreak havoc in victims’ lives through major inconvenience and annoyance. At worst, cybercrime can lead to financial ruin and potentially threaten a victim’s reputation and personal safety. Having your identity stolen can be scary and invasive and have damaging effects on your finances, medical records and reputation. If you become a victim, knowing how to respond and report the incident is vital.” Visit their site for some tips and resources to help you recover.
Provided by RISC Management and Consulting and the Privacy and Security Institute (PSI)




















You must be logged in to post a comment.