If you feel helpless like many people do, here are things you can do to take back control. Taking control can reduce depression, anxiety, and feelings of helplessness.

First here’s a summary on what’s going on: According to Centers for Disease Control and Prevention (CDC), “globally, approximately 170,000 confirmed cases of corona virus disease 2019 (COVID-19) caused by the 2019 novel corona virus (SARS-CoV-2) have been reported, including an estimated 7,000 deaths in approximately 150 countries”(2020, March 27).
The World Health Organization (WHO) reported that the current COVID-19 pandemic is caused by a coronavirus named SARS-CoV-2. Coronaviruses (CoVs) are a large family of viruses, several of which cause respiratory diseases in humans, from the common cold to more rare and serious diseases such as the Severe Acute Respiratory Syndrome (SARS) and the Middle East respiratory syndrome (MERS), both of which have high mortality rates and were detected for the first time in 2003 and 2012, respectively.
- Frontline healthcare workers worldwide even in normal times face vast challenges when it comes to prioritizing their own health; that strain is greatly compounded amid a public health crisis.
- Already in response to COVID-19, thousands of healthcare workers are falling ill. In China, nearly 3,400 healthcare workers have been infected, and 22 have died—not just from the virus itself, but from cardiac arrest and other conditions caused by overwork and exhaustion. In Italy, at least 2,629 health workers have gotten sick—8.3 percent of total cases in that country. And here in the US, dozens of frontline workers have already been infected, with many others having to self-quarantine.
- The burdens—both acute and chronic—that healthcare workers face today are leading to a dangerous burnout epidemic, which will have devastating consequences for both providers and patients.
Here is some important terminology:
- A virus that is regularly transmitted from an animal to a human is called a zoonotic virus. When a virus passes from animals to humans for the first time it is called a spillover event.
- SARS-CoV-2 is the corona virus that is causing the current COVID-19 respiratory disease in humans.
- Increasing evidence suggests that a lost sense of smell, known medically as anosmia, may be a symptom of COVID-19. This is not surprising, because viral infections are a leading cause of loss of sense of smell, and COVID-19 is a caused by a virus.
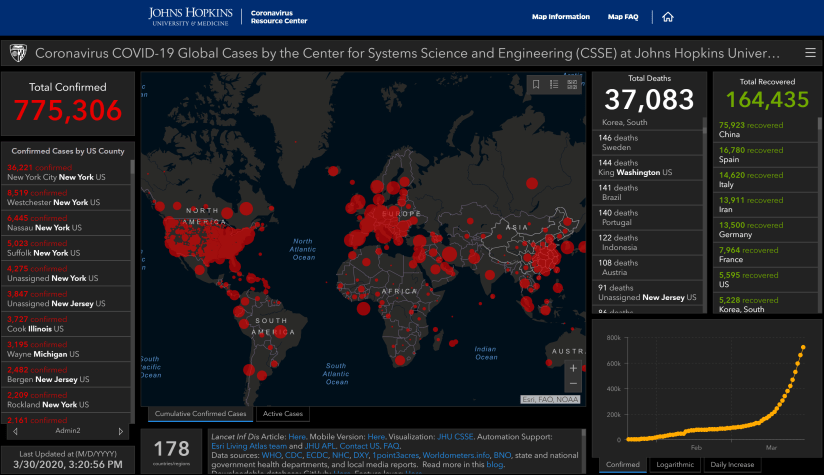
Here are the numbers from John Hopkins Coronavirus Resource Center as of March 30, 2020.
- Total Confirmed: 775,306 (Johns Hopkins)
- Total Deaths: 37,083 (Johns Hopkins)
- 2486 Deaths from the U.S. (Johns Hopkins)
- 790 Deaths in New York City, NY (Johns Hopkins)
Please view real time changes from the Johns Hopkins website for current information as the details change every minute.




Practice Wellness While Staying at Home
The next time you’re feeling anxious try this simple relaxation technique:
- Inhale slowly and deeply through your nose. Keep your shoulders relaxed
- Exhale slowly through your mouth. As you blow air out, purse your lips slightly, but keep your jaw relaxed
- Repeat this breathing exercise for several minutes
Moving and Stretching, Indoors and Out
- Exercising regularly can provide a sense of well-being
- You might have increased energy, sleep better at night, have sharper memories and an increased feeling of being relaxed and positive about yourself
- Regular exercise can assist in relieving stress, depression, and anxiety
- “No matter your age or fitness level, you can learn to use exercise as a powerful tool to feel better” (HelpGuideOrg International)
- Gardening and hiking outdoors, and taking notice of the natural world, helps alleviate anxiety and improve well-being. In fact many National Park Service parks are entrance-fee free right now because of the pandemic!
- “Home air can get stuffy,” going outdoors daily for 15 minutes of fresh air and sunshine (Harpreet Gujral, DNP, FNP-BC), or open some windows on opposite sides of your home to encourage healthy airflow
- Walking outdoors occasionally ensures your body can produce endogenous vitamin D when ultraviolet rays from sunlight strikes your skin to trigger vitamin D synthesis
- Without sufficient vitamin D, bones can become thin, brittle, or misshapen (National Institutes of Health)
- Vitamin D has other roles in the body, including modulation of cell growth, neuromuscular and immune function, and reduction of inflammation
Fitness Plan: Get Out & Exercise
- Make it a fun activity
- Use your online calendar and add activities to keep in shape
- Take control of your social distancing by creating your fitness plan
Physical activities— walking, running, biking, swimming (no public pool at this time is encouraged), gardening, dancing or other aerobic exercise is best to provide a good workout for your heart!  “Runner’s high” is real, research shows. During exercise, the brain produces endorphins — natural chemicals similar to morphine that cause a feeling of happiness. For maximum endorphin benefit, get at least 30 minutes of aerobic exercise three to four times a week, advises the American Council on Exercise (WebMD).
“Runner’s high” is real, research shows. During exercise, the brain produces endorphins — natural chemicals similar to morphine that cause a feeling of happiness. For maximum endorphin benefit, get at least 30 minutes of aerobic exercise three to four times a week, advises the American Council on Exercise (WebMD).
Endorphins and Beta-endorphins
Endorphins are part of the “brain chemicals known as neurotransmitters, which function to transmit electrical signals within the nervous system” (Sprouse-Blum, A. S., Smith, G., Sugai, D., & Parsa, F. D., 2010)
- Endorphins act on the opiate receptors in our brains, to decrease pain and enhance pleasure, resulting in a feeling of well-being similar to morphine and codeine
- Endorphins became a loose term with regards to endogenous neuropeptides and peptides with opioid-like activities
- Beta-endorphins are neuropeptides involved in pain management, possessing morphine like effects, and are involved in natural reward circuits such as feeding, drinking, sex and maternal behavior
- Beta- endorphins are endorphins produced in the pituitary gland that is a powerful pain suppressor
Relaxation, Endorphin, Strength, Flexibility, and Balance Control
“Yoga is a mind and body practice with a 5,000-year history in ancient Indian philosophy” (Nichols & Murrel, 2018). Practicing Yoga and Tai chi can assist with relaxation and contributes to production of endorphins.
- Involves deep breathing and calming exercises, Yoga/Tai chi also relieves stress and promotes well-being
- Became a popular form of physical exercise especially when combined with weights (my favorite method)
Yoga Tips + Advice for Beginners
Here’s a fun fitness quiz
Eating Well and Facts About Nutrition
- Most important feature of a good diet is variety
- Eating a healthy diet is not about strict limitations, staying unrealistically thin, or depriving yourself of the foods you love
- Healthy eating doesn’t have to be overly complicated
- Foundation of healthy food source would be to replace processed food with real food when possible
“To make sure your eating plan contains all the nutrients you need, choose a rainbow of colorful foods. The pigments that give foods their color are also the nutritious substances that can reduce your risk of cancer and chronic diseases like heart disease.
Of course, foods with the most “pigment power” are mostly fruits and vegetables — yet another reason to fill your plate with these fiber-filled, low-calorie, fat-free, super foods! Eaten together, fruits and vegetables pack an even bigger punch in reducing free radicals — unstable molecules in the body that damage cells and are thought to contribute to the development of many diseases.”(WebMD)
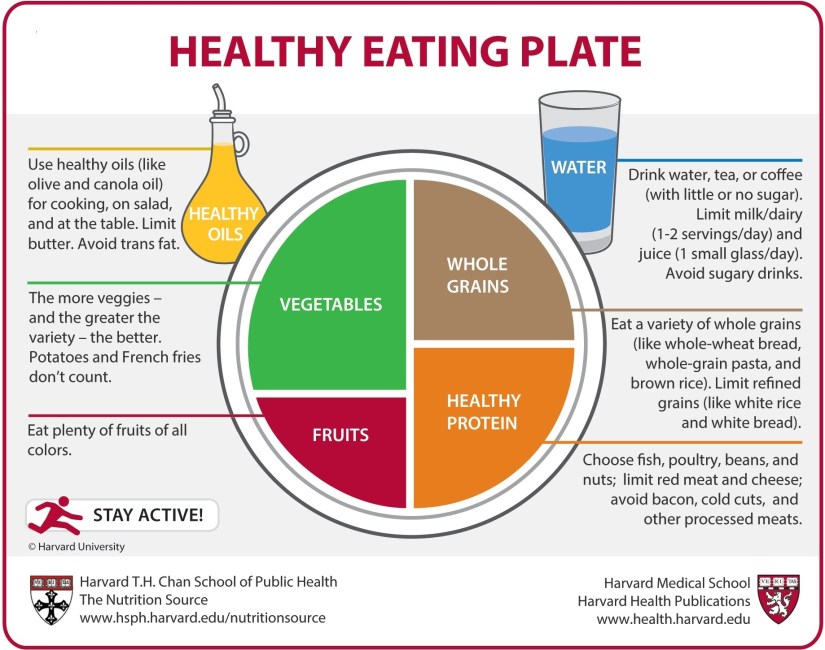
Here’s an easy to understand representation for a variety of foods and colors
From the Harvard School of Public Health with Copyright © 2011, Harvard University. For more information about The Healthy Eating Plate, please see The Nutrition Source, Department of Nutrition, Harvard T.H. Chan School of Public Health, www.thenutritionsource.org, and Harvard Health Publications, www.health.harvard.edu.
Antioxidants
Antioxidants are your friends when it comes to removal of those nasty free radicals. Eating a diet abundant with antioxidants has been linked to a multitude of health-promoting, disease-fighting activities in the body. “Free radicals and other reactive oxygen species (ROS) are constantly formed in the human body. Free‐radical mechanisms have been implicated in the pathology of several human diseases, including cancer, atherosclerosis, malaria, and rheumatoid arthritis and neurodegenerative diseases. When produced in excess, ROS can cause tissue injury.” (Phaniendra, A., Jestadi, D., and Periyasamy, L., 2014, July 15) Eating a diet abundant with antioxidants has been linked to a multitude of health-promoting, disease-fighting activities in the body. 

 Antioxidant-rich foods include:
Antioxidant-rich foods include:
- Vitamin A and beta-carotene: Pumpkin, squash, carrots, spinach, sweet potatoes, cantaloupes, dark leafy greens, and mangoes
- Vitamin C: Citrus fruits, strawberries, bell peppers, cauliflower, broccoli, tomatoes, sweet potatoes, asparagus
- Vitamin E: Vegetable oil, almonds, whole grains, wheat germ, sweet potatoes, yams

- Selenium: Salmon, haddock
Without adequate vitamin D, your body can’t properly absorb calcium, leading to a higher risk of broken bones , especially in the elderly. A recent Swiss study suggests that elderly folks may be able to reduce their risk of injury from falls with vitamin D supplementation, however the best source of this nutrient is sunshine.  Other good sources include:
Other good sources include:
- Fortified milk and some orange juices. Juice manufacturers are now adding both calcium and vitamin D for better absorption
- Salmon and mackerel
- Eggs
 The best sources of calcium are dairy foods, though it’s also found in:
The best sources of calcium are dairy foods, though it’s also found in:
- Dark leafy greens
- Fortified products like cereal and orange juice
Here are some basic things we know with regards to vitamins and minerals:
- Vitamins and minerals have no calories.
- All vitamins and minerals can be found in foods.
- If your diet has too little of a vitamin or mineral over a long period of time, you will develop a deficiency.
- The best form of most vitamins and minerals is the kind you get from food
At Your Home Office
Here are some suggestions:
- Being organized is the key
- A task list is a must
- Many types to choose from to get organized such as using the Trello application, your own Outlook Calendar, One Note, Evernote, and many more
- Nothing wrong with old school note book as long as you add tabs with titles
- Use a room that is away from the family or noise
- Schedule breaks, lunch time, meetings, and office hours
- If sharing office space with other family members, schedule office calls and share with family members (provides quite time)
- Most importantly, get dressed and showered!
 For my own experience, I like using a room that has a window, outdoor lighting, and I added a slim desk to make space for my Supersticky easel pad so I can visualize and organize my projects. I also included a separate portable table for organizing work documents, office supplies, and miscellaneous items. Remember time management is the key to creating a work environment while staying at home.
For my own experience, I like using a room that has a window, outdoor lighting, and I added a slim desk to make space for my Supersticky easel pad so I can visualize and organize my projects. I also included a separate portable table for organizing work documents, office supplies, and miscellaneous items. Remember time management is the key to creating a work environment while staying at home. 
Staying Focused
- Eliminate distractions – create a calendar with the family to include quiet time, study/work time, and fun time such as when TV can be turned on
- Ask your team/coworker to have less phone calls in order to get work done, schedule work calls or webinars
- Get a good night’s sleep
- Find the right time of day for you where you can do the most work
- Allow yourself to take breaks! Breaks enable you to be more productive during focus time.
Rest and Relaxation
- Adults need between 7 to 9 hours of sleep per night to function at their best
- Deprivation of sleep makes us sleepy and results in poor performance
- Sufficient sleep improves our alertness, mood, and performance
- Relaxation and stress reduction correlation is true
- Time management will decrease stress and improve work performance
“No matter what the cause, stress floods your body with hormones. Your heart pounds, your breathing speeds up, and your muscles tense.
This so-called “stress response” is a normal reaction to threatening situations, honed in our prehistory to help us survive threats like an animal attack or a flood. Today, we rarely face these physical dangers, but challenging situations in daily life can set off the stress response. We can’t avoid all sources of stress in our lives, nor would we want to. But we can develop healthier ways of responding to them.” (Harvard Health Publishing)
Practicing Mindfulness
Include stress management techniques to reduce your stress from having to work from home and dealing with family trying to do the same in the same space. Make an agreement with yourself to set aside time for relaxation during this stressful time. There are many techniques available online that are only 5 minutes long. I found that starting my day with stretches makes me feel great and ready for the day. After a long day of staring at the computer, talking with clients and coworkers, it is important to remove yourself from the demands from work and de-stress. However, if needed after a demanding project, don’t wait for the end of your day to get rid of tension before it becomes a headache or indigestion.
-
Choose a quiet place to have an uninterrupted exercise for de-stressing
-
Try yoga or Tai-chi (see link for a 5 minute module for beginners)
-
Practice the 1-Minute Mindfulness Exercise
-
Don’t just sit home and watch television, use free time to improve your home, space, and self
-
Practice self-reflection to build emotional self-awareness with a goal of understanding your emotions, strengths, weaknesses, and driving factors in order to become more confident
Six relaxation techniques from experts that can help you evoke the relaxation response and reduce stress. Follow the link for the full description:
1. Focusing your breath
2. Progressive muscle relaxation
3. Guided imagery
4. Mindfulness meditation
5. Yoga, tai chi, and qigong
6. Repetitive prayer or any phrase
20 Ideas to Help You Survive & Thrive Through the Epidemic
Visit the website for ideas and improving your current self. In the meantime, here are the top five that I thought were interesting and easier to achieve (Psych Central).
- Declutter your house. Is your clutter getting out of control because of your busy life? Use this time to get organized. Go through the papers and unnecessary objects in your house and sort it. Make 4 piles and label them: Keep, Garbage, Donate, Maybe. It will feel so good. It’s you taking control in an uncontrollable situation. The trick is to take the time and put things where they belong. For example, if they are paper work, create a file and put it away, for photos, put in a clear container so you can identify it easier for the future (albums or scanning them), take the donation right away, do not put in your garage!
- Learn a new language. It has so many benefits. It not only improves your brain, but it also connects you to a different culture and that is a good thing in today’s world. I used an app from my phone called Duolingo. It is fun and will give you a lot of self-satisfaction.
- Improve your cooking. Cooking is a form of creativity and it’s also a way to practice self-care. It may also be safer than buying prepared foods during a pandemic!
- Explore new music.It’s easy to fall into a rut of listening to the same artists or styles over and over. Get yourself out of it and try something new. I get suggestions from my friends and family then I use the music selection while exercising. Included in this is learning an instrument and playing the guitar is the simplest since there are plenty of online information such as free websites and videos.
- Improve your relationship with an important person.This might be anyone who you’ve always wanted to have a better relationship with. Amazing progress can be made when you have the time and energy to focus on it. All it takes is one phone call or just send a text.
Thank you for your time and enjoy We’ve added a reference list to keep you informed

References
Ankrom, C. (2020, January 23). Deep Breathing Exercises to Reduce Anxiety. Very Well Mind. https://www.verywellmind.com/abdominal-breathing-2584115
Aruoma, O. (1998). Free radicals, oxidative stress, and antioxidants in human health and disease. Journal of the American Oil Chemist’s Society. DOI.org/10.1007/s11746-998-0032-9
Center for Disease Control and Prevention. (2020, March 26). Severe Outcomes Among Patients with Coronavirus Disease 2019 (COVID-19) — United States, MMWR Morb Mortal Wkly Rep 2020;69:343-346. DOI: http://dx.doi.org/10.15585/mmwr.mm6912e2
Harvard T.H. Chan School of Public Health. (2011). The healthy plate. The Nutrition Source. https://www.hsph.harvard.edu/news/press-releases/firstrespondersfirst-covid-healthcare-workers/
Johns Hopkins University and Medicine. (2020). Coronavirus Resource Center. https://coronavirus.jhu.edu/map.html
National Institutes for Health (NIH). (2020, March 24). Vitamin D. Health Information. https://ods.od.nih.gov/factsheets/VitaminD-HealthProfessional/
Nichols, H. and Murrell, D. (2019, September 25). How does yoga work? Healthline Media UK Ltd. https://www.medicalnewstoday.com/articles/286745
Phaniendra, A., Jestadi, D., and Periyasamy, L. (2014, July 15). Free Radicals: Properties, Sources, Targets, and Their Implication in Various Diseases. Indian Journal of Biochemistry. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC4310837/
Robinson, L., Segal, J., and Smith, M. (2019, June). Mental health benefits of exercise. HelpGuideOrg International. https://www.helpguide.org/articles/healthy-living/the-mental-health-benefits-of-exercise.htm
Sprouse-Blum, A. S., Smith, G., Sugai, D., & Parsa, F. D. (2010). Understanding endorphins and their importance in pain management. Hawaii medical journal, 69(3), 70–71. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3104618/
World Health Organization . (2020, March 27). Coronavirus disease (COVID-19) Pandemic. Emergencies and Diseases. https://www.who.int/emergencies/diseases/novel-coronavirus-2019 Yoga Journal (2020).
Yoga 101. Cruz Bay Publishing, Inc. https://www.yogajournal.com/







 It is the perfect time to follow some security tips for both your home and work.
It is the perfect time to follow some security tips for both your home and work. 





















You must be logged in to post a comment.