Challenges of Meaningful Use
Meaningful Use (MU) is the adoption of a certified Electronic Health Record (EHR) technology with a focus on improving quality, safety, efficiency, and reducing health disparities in the clinical/hospital setting. The idea is to increase patient engagement to improve care coordination while maintaining the privacy and security of the patient’s Protected Health Information (PHI).
According to Milan (July 27, 2015) “After a day spent hearing from health IT experts about information blocking practices, Republican Sen. Lamar Alexander, chair of the Senate Health, Education, Labor & Pensions Committee, said Thursday afternoon that he’s asked HHS to consider a delay of Stage 3 meaningful use”. The Department of Health and Human Services (HHS) is the U.S. government’s main agency for enhancing and protecting the health and well-being of all Americans.
Here are some quotes from Senator Lamar Alexander:
“Let’s not impose on physicians and hospitals a system that doesn’t work…”
“We want something physicians buy into, rather than something they dread…”
It is important to update and improve our current way of keeping health records as well as a more appropriate way to share health information with other providers. The quality of the EHR tool becomes the most desirable trait it seems. Remembering HIPAA where the importance of assessing all of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of all Protected Health Information (PHI) is required. However, each medical provider is unique in their operational environment with their own set of variables and must be factored in to the equation.
Another important piece of information according to McCarthy (July 22, 2015):
“Stage 3 of meaningful use for EHR implementation requires providers to send electronic summaries for 50 percent of patients they refer to others, receive summaries for 40 percent of patients that are referred to them and reconcile past patient data with current reports for 80 percent of such patients. If other providers do not send electronic summaries, however, the provider who was supposed to receive them will fail to meet the second and third requirements.”
Probst (2014) mentioned from an interview that Intermountain Healthcare is Stage 2 Certified in 2014 but will not be attesting at this time.
The Agency for Healthcare Research and Quality (AHRQ, March 26, 2015) provided some research data on barriers to meeting the stage 3 criteria for Meaningful Use:
- Lack of provider and practice staff time – 69%
- Complexity of required workflow changes – 68%
- Difficulty with electronic exchange of information – 65%
- Direct Financial Costs – 54%
- EHR design and functions do not easily support care coordination – 51%
Readiness to meet criteria results:
- Only 11% of those who participated in the research are able to meet all of the criteria
AHRQ’s mission is to “bring about evidence to improve health care quality and safety, increase accessibility, equitability and affordability within the HHS and other partners. Their objective is to ensure that the evidence is understood and employed.
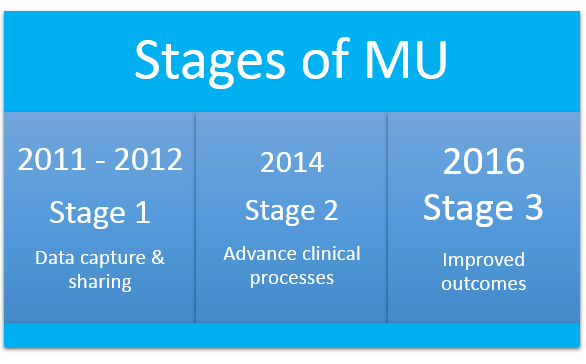
For more information on Stages of Meaningful Use Click the link above
These are only some views on the subject of Meaningful Use, but there are many standards, policies, ideas that are available from other organizations that might be helpful.
Our work here at RISC Management has enabled us to view firsthand the privacy and security challenges of Meaningful Use, and of course HIPAA and HITECH. These are significant challenges that the Providers must meet, but they are reasonable and attainable.
For more information on Risk Analysis Click the link above
References
Agency for Healthcare Research and Quality. (March 26, 2015). Informing stage 3 meaningful use requirements through evidence: Webinar. Retrieved from https://www.youtube.com/watch?v=nQrMKcq0VAM
McCarthy, Jack. (July 22, 2015). Stage 3 meaningful use ignores market realities. Retrieved from http://www.healthcareitnews.com/news/brookings-meaningful-use-stage-3-ignores-market-realities
Meaningful Use. (2015) Definition. Retrieved from http://www.healthit.gov/providers-professionals/meaningful-use-definition-objectives
Miliard, Mike. (July 23, 2015). Senate suggests stage 3 MU delay. Retrieved from http://www.healthcareitnews.com/news/senate-call-stage-3-mu-delay?mkt_tok=3RkMMJWWfF9wsRohuKTPZKXonjHpfsX57e8uUKOylMI%2F0ER3fOvrPUfGjI4GRMVkI%2BSLDwEYGJlv6SgFQ7LHMbpszbgPUhM%3D
Probst (2014). CIO on MU stage 2: Certified but not attesting. Retrieved from http://bcove.me/kt82385m


















You must be logged in to post a comment.