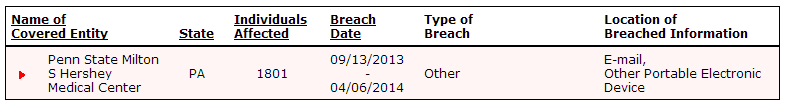
Just last month, a Pennsylvania-based hospital suffered a breach of patient data caused by unauthorized access and transmission of PHI by an employee. The 551-bed Penn State Milton S. Hershey hospital discovered through an internal investigation that a lab technician accessed and transmitted protected health data outside of the hospital’s secure network. The key in this breach was that the employee was authorized to work with PHI but in this case did not access and transmit the PHI securely. He used his own USB device and sent patient data through his own personal email address to two physicians.
The important thing to note in this situation is what your organization can do to avoid a situation like this: train your workforce. Not only is workforce training required by HIPAA, it is a prudent means of improving efficiency and confidence in your workforce. Many organizations believe that their biggest threat lies outside their walls. While it is a smart business decision to implement security controls to prevent intrusions from external threats, your organization should also prioritize properly training your workforce. Below is a list of the most investigated issues as noted in the OCR Enforcement highlights.
From OCR Enforcement highlights:
From the compliance date to the present, the compliance issues investigated most are, compiled cumulatively, in order of frequency:
- Impermissible uses and disclosures of protected health information;
- Lack of safeguards of protected health information;
- Lack of patient access to their protected health information;
- Uses or disclosures of more than the minimum necessary protected health information; and
- Lack of administrative safeguards of electronic protected health information.
Security Rule Enforcement Results as of the Date of This Summary
With regard to the subset of complaints specifically pertaining to the Security Rule, since the OCR began reporting its Security Rule enforcement results in October 2009, HHS has received approximately 880 complaints alleging a violation of the Security Rule. During this period, HHS closed 644 complaints after investigation and appropriate corrective action. As of May 31, 2014, OCR had 301 open complaints and compliance reviews.
Here is the direct link to the Breaches Affecting 500 or More Individuals: http://www.hhs.gov/ocr/privacy/hipaa/administrative/breachnotificationrule/breachtool.html

















You must be logged in to post a comment.